I would like to bring a discussion originally raised in our gitlab.
Original ticket has been created for the Web Verification App, but this topic also applicable to Seal add-ons and Extensions.
Generally, verification flow consists of three steps:
- Reading QR code data and obtaining status id
- Reading array of statuses for specified status id
- Statuses verfification
- Verification of the attachments
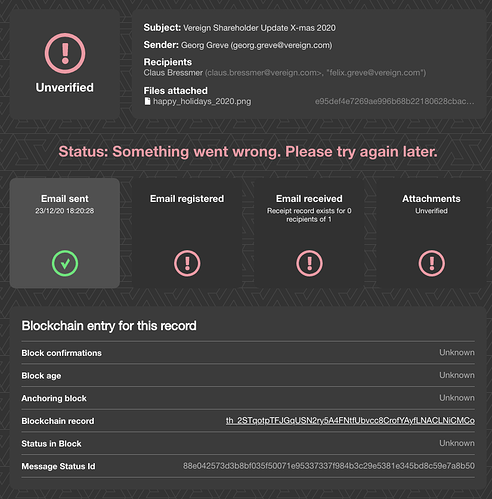
What possibly could go wrong during the whole verification routine
Reading QR code data
As we know, HEAD part of the QR code data being passed as base64 encoded protobuffer message using ?q= argument of the query string. (e.g: https://office.app.vereign.com/?q=CiDENc3Vva99Emghtc7xA4YkspjDlR7feoTqgQSuRIiT6RIgrhgyERdaNCyFOsUjkZJeXfY7K2jQ8tIvuRlSsqZZgJk=×tamp=1610541100482)
- First error might happen during the protobuffer decoding of the
?q=base64 string in case q is invalid protobuffer message. - Next step is fetching of the encrypted TAIL part from CDN. Tail might not be available due to async nature of uploading data to the CDN. We should show “pending” state.
- Final step is decryption of the assembled QR code data. Decryption might fail in case one of the keys broken somehow.
Once the whole routine is done, application obtains the next structure:
{
statusId,
sender,
subject,
date,
recipients,
attachments,
senderPublicKeyUuid;
}
Reading array of statuses
- First of all, statuses might be pending in backend queue and not available yet.
- Once statuses are fetched, application reads public key of the sender from CDN. Public key might not be available yet due to async nature of uploading data to CDN.
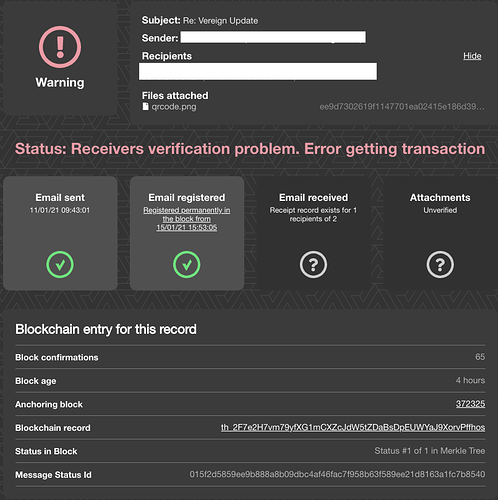
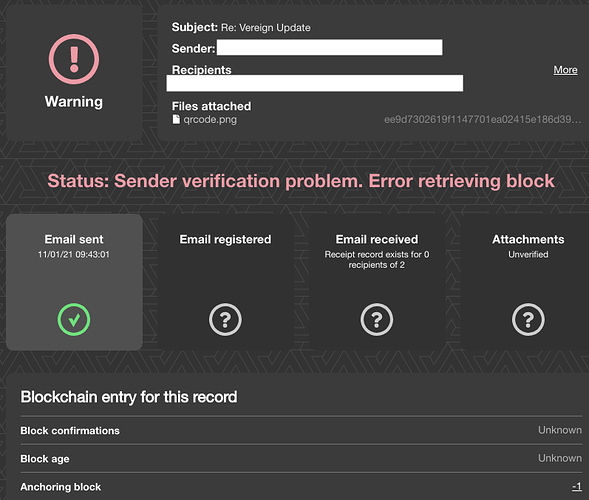
- After that flow verifies status of the sender using the public key retrieved in previous step. This verification might fail as well in case something is wrong with either signature or public key. This would mean that status might not belong to the original sender.
- There’s also a possibility that more than one status of the sender present in the array due to a bug in browser extension/add-on. Currently this case is handled as verification error.
- The last step is selection of recipients statuses by taking everything in the array except for status of the sender. Due to possible bug in extension, status of the recipient might be duplicated as well, but landing page at the moment has no way to detect that. It’s just going to show something like “Receipt record exists for 4 recipients of 2”
Verification of the statuses
For every status in the array:
- Application checks whether blockchain transaction hash exists. If no, further verification of the status does not make sense yet, and status considered as pending.
- Application reads transaction providing transaction hash. A transaction might not be available due to various reasons. e.g. consequences of the attack 51%, or blockchain node malfunctioning.
- Next step is retrieval of the name of file with merkle tree from transacion. It happens by calling publicly hosted aeternity compiler.
- After that app retrieves merkle tree nodes from CDN. I assume there’s a chance that merkle tree data might not be uploaded yet as well.
- Next step is verification of the merkle tree.
- Last step is retrieval of the block information which might fail in case the block has been reverted.
Verification of the attachments
Verification happens by ensuring that every signature presented in QR code data is also exists in Sender status data. I am not sure whether this step is correct at all, but I don’t see the other way, assuming that we don’t have access to the contents of the attachments.
For most of the steps in this flow a simple Network error might happen for various reasons. E.g. due to interruption of the internet connection.
Related topic: Check message status using Vereign Seal
@georg.greve please let me know whether I chose not correct place for this topic.